What is lean cybersecurity
Discover lean cybersecurity and how it can help teams reduce waste and deliver high-impact results
Lean cybersecurity is a systematic approach to eliminating waste and streamlining security operations to produce maximum value for stakeholders. The concept of lean cybersecurity is inspired by lean manufacturing, an industrial optimisation approach aiming to use fewer resources and efficient processes to meet customer demands.
Lean cybersecurity provides a critical operational advantage for security teams navigating the dual pressures of evolving threats and increasing scrutiny over costs and value output. By adopting efficiency holistically, attention can be focused on activities that have the most impact on stakeholders, thereby reducing wasted effort. With lean cybersecurity, operations become more inspectable and measurable. Teams have the diagnostic tools needed to systematically align priorities with business objectives, without compromising on security goals or budget discipline.
In this article, we will examine the foundational principles of lean manufacturing, discuss how they apply to cybersecurity and highlight some methodologies you can use in your security program today.
Lean manufacturing principles
Lean manufacturing originated as a response to inefficiencies in traditional mass production, with roots tracing back to post-World War II Japan. Faced with limited resources and intense economic pressure, Toyota pioneered a new system of production that maximised waste reduction, efficiency and quality. This approach evolved into what is now known as the Toyota Production System (TPS), which laid the foundation for modern lean manufacturing. Toyota’s model redefined global manufacturing by shifting focus from maximizing output to maximizing value for the customer.
At the core of Toyota’s approach is the “Toyota Production System House,” a visual framework often depicted as a house supported by three main pillars: Heijunka (Levelling), People and Teamwork, and Jidoka (Built-in Quality). These pillars uphold the roof of the house, which represents the goal of delivering the highest quality and value of outputs while sustaining the lowest costs and shortest possible lead times.
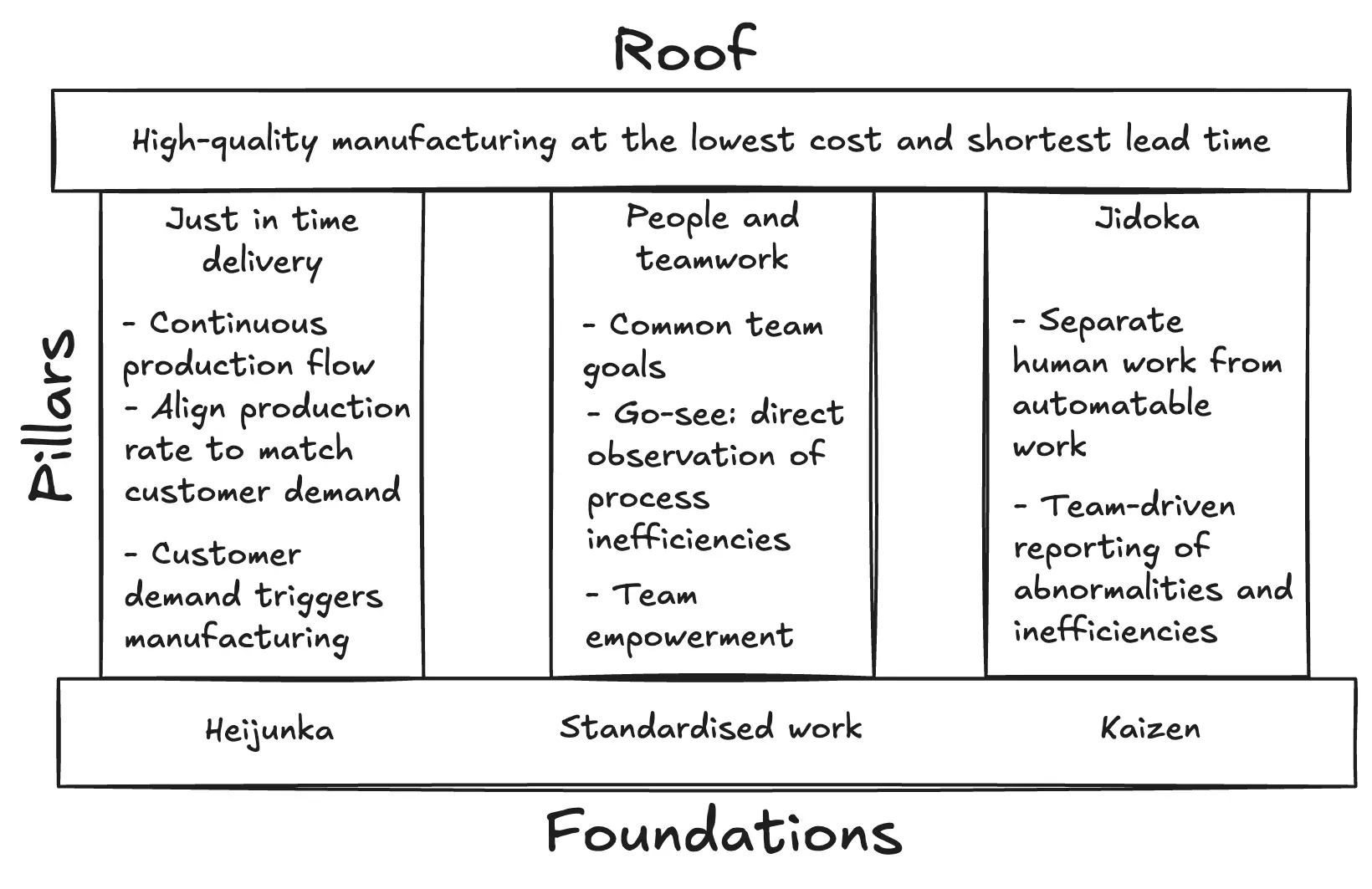
Each pillar plays a distinct role in the system:
The Heijunka (levelling) pillar, is the process of smoothing production schedules by evenly distributing volume over time. This reduces the burden of demand fluctuations on workers and equipment, enabling a steady production flow. Heijunka enables the Just-in-Time goal by ensuring parts and products are manufactured at the right time and in the right quantity, reducing overproduction.
The People and Teamwork pillar is built on standardized work, the Go-See principle (Genchi Genbutsu), and shared objectives. Standardizing work ensures repeatability and clarity in operations. The Go-See principle promotes direct observation to gain accurate insights and foster problem-solving. Common goals align teams and stakeholders, increasing collaboration and ownership. Together, these elements create a culture where people are empowered, informed and primed for sustained operational excellence.
The Jidoka (built-in quality) pillar, is enabled through the principle of Kaizen (continuous improvement). Kaizen involves every employee in identifying inefficiencies and proposing improvements. When embedded in daily work, Kaizen enables teams to detect and address problems at the source, often through automation with human oversight. This ensures that quality is maintained throughout the process, not just at the end, and supports the Jidoka goal of preventing defects and enabling intelligent automation.
Through these three pillars, Toyota’s manufacturing philosophy delivered an adaptable system that prioritised efficiency and quality. More importantly, it shifted human work away from automatable tasks and towards value-enhancing activities.
Applying lean principles to cybersecurity
The principles of lean manufacturing translate directly to cybersecurity, where the aim is also to deliver high-value protection and risk reduction at minimal cost and lead time. Just as factories pursue flow and efficiency, security operations must deliver high-value protection services without wasting time, effort and money.
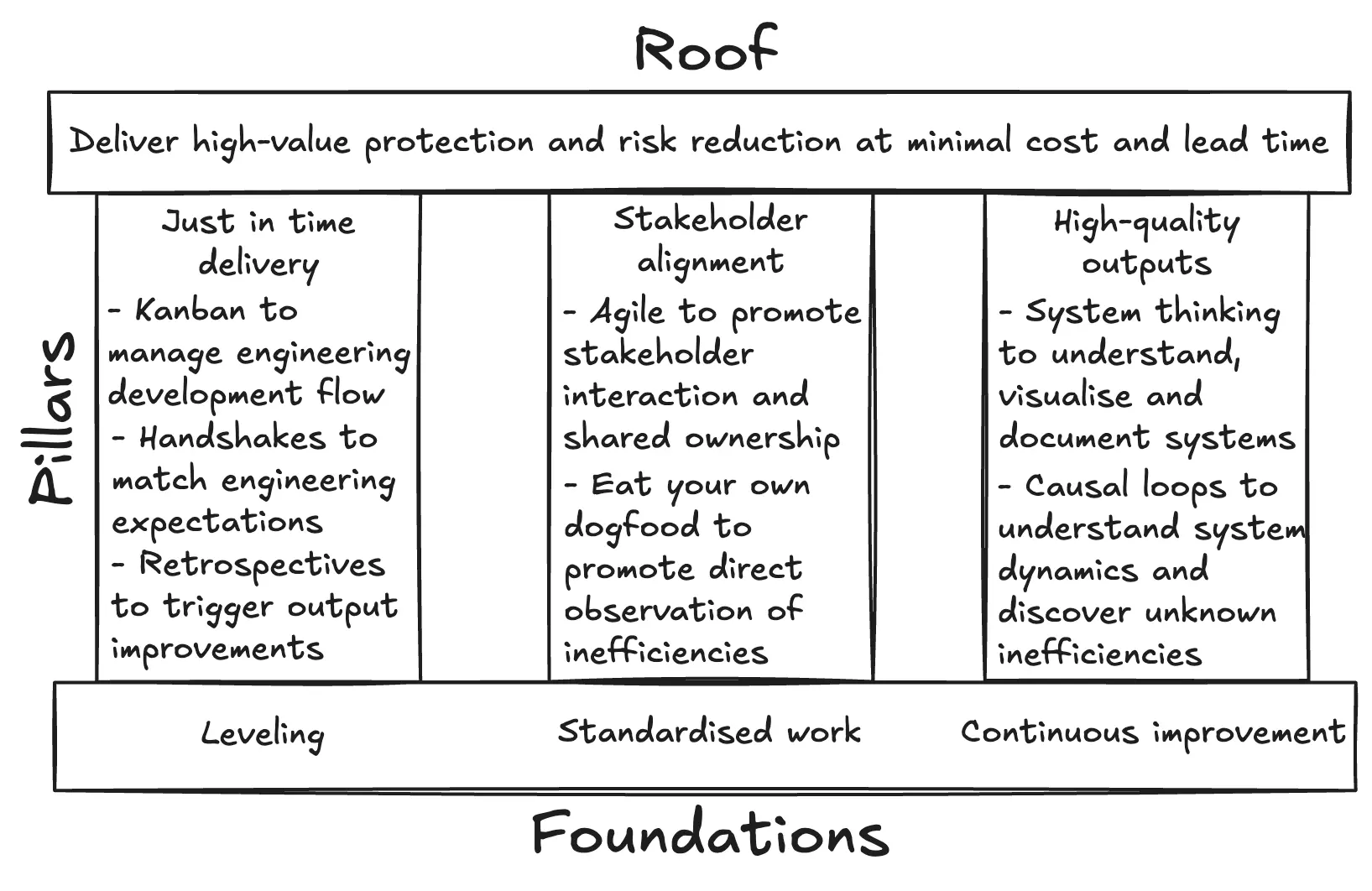
Levelling is essential to balance workloads in security operations. Teams must often manage surges in operational demands while delivering consistent risk reduction and adapting to shifting internal requests. A levelling system smooths this variability by structuring work intake, clarifying priorities, and maintaining response capacity. This ensures teams remain incident-ready without burnout, and that strategic projects, such as control improvements or risk reviews, are not continually displaced. Sustainable operations depend on predictability, which only levelling systems can provide.
The People and Teamwork pillar is equally vital. Here, security teams adopt systems to standardise workflows and to promote direct observation of process inefficiencies. Additionally, they adopt systems to align with stakeholders around relevant business goals. By adopting these principles, security teams become value-generating partners rather than siloed cost centres.
Continuous improvement principles are key to optimising and scaling security programs. Teams must regularly inspect and refine their processes and tools, driving toward greater automation and efficiency. The goal here is to free human attention for higher-value tasks, namely handling complex incidents, identifying root causes of failure and improving team workflows. These activities enhance operator quality of life and reduce operational fatigue. In high-maturity scenarios, automation can shift team attention to supporting revenue-generating initiatives such as go-to-market activities (like customer questionnaires) or product enhancements (like regular security architecture reviews).
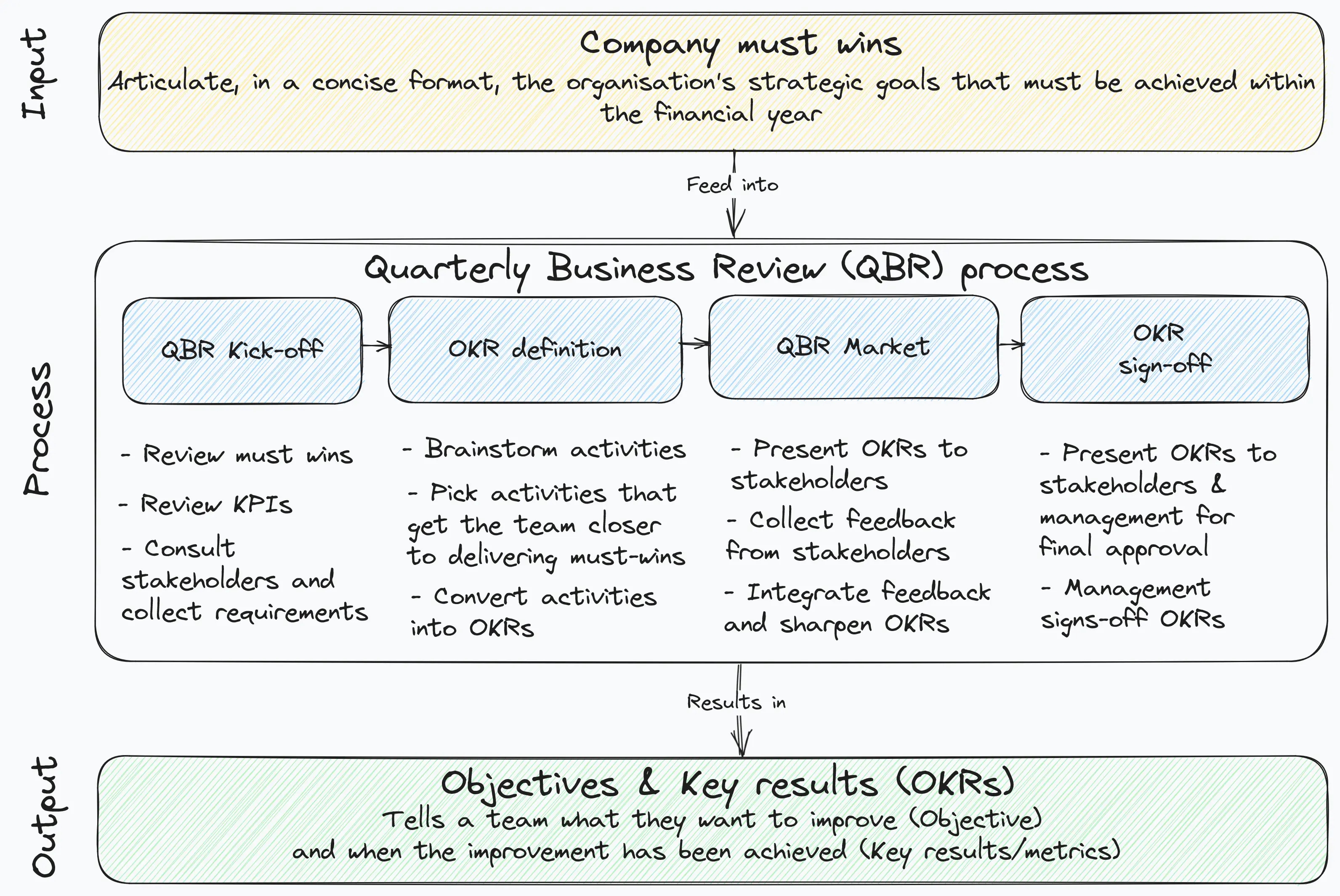
Implementation methods
Concepts like workload balancing, people and teamwork and continuous improvement are intuitively appealing. Most cybersecurity professionals would agree they are essential to any effective program. However, it is often less clear how to apply these principles in practice. Despite widespread agreement on their importance, organizations struggle to adopt them.
Fortunately, three straightforward implementation methods can be easily adopted that provide strong directional guidance toward building a lean cybersecurity program. However, it’s critical to recognize that these methods are only the starting point. Their true impact depends not only on adoption but also on consistent execution, reinforced by unwavering leadership support and organizational buy-in. Without that, implementation initiatives will struggle to take root.
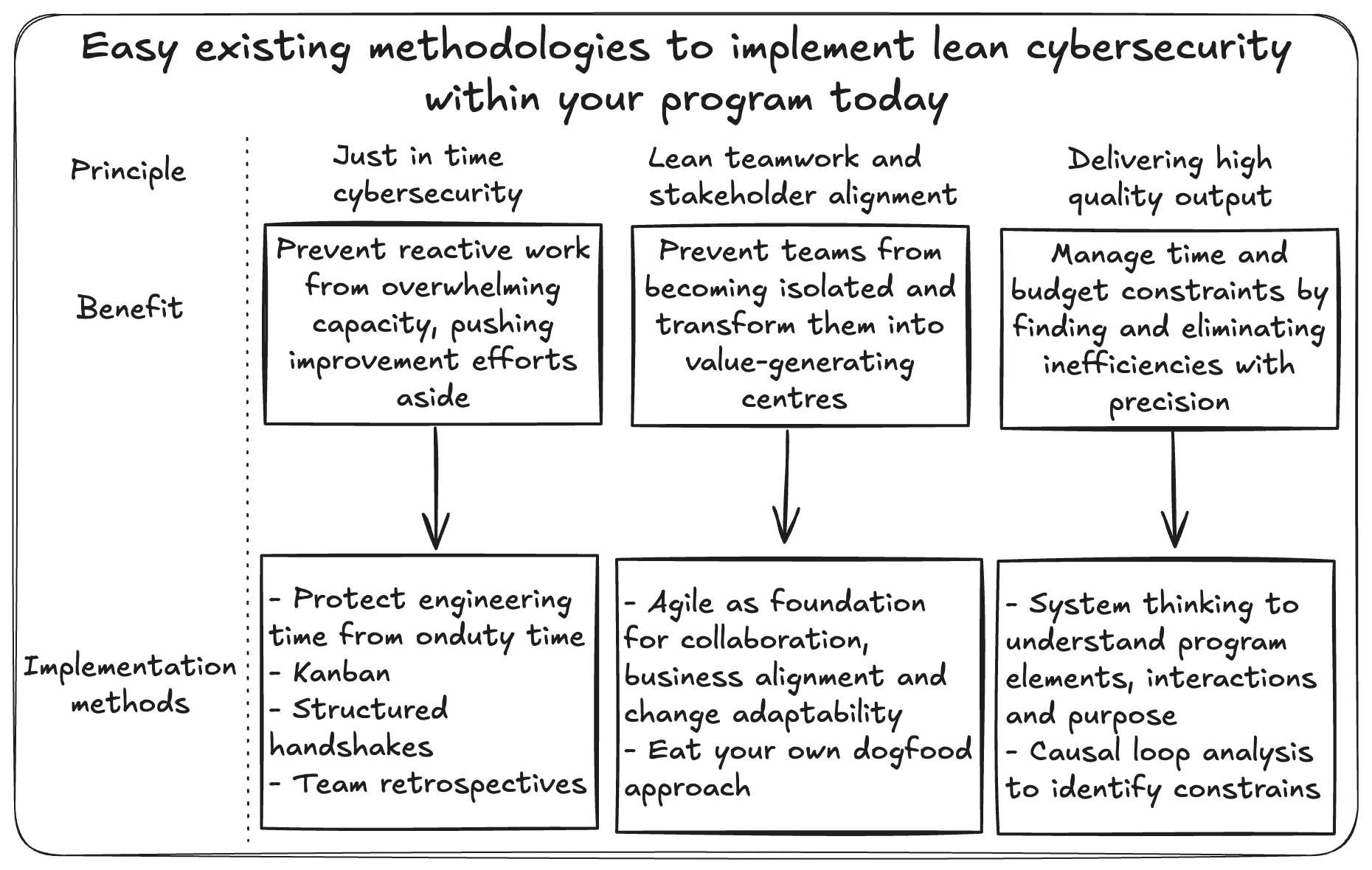
Achieving just-in-time cybersecurity
To achieve levelling within cybersecurity operations, teams must implement a consistent system to balance fluctuations in operational demand. Without this balance, reactive work quickly overwhelms capacity, pushing improvement efforts aside. Protecting time for engineering initiatives that enhance efficiency and reduce costs is essential. Levelling ensures both reactive and proactive workstreams progress in tandem, maintaining operational readiness without sacrificing long-term improvement.
To effectively protect engineering time, it must be separated from on-duty periods, during which analysts must remain fully focused on incident monitoring and response. However, when analysts transition off-duty, they must work to translate their frontline experience into meaningful improvements.
Three simple yet powerful methods enable this: using Kanban to prioritise engineering improvements, holding structured handshake meetings to offload complex tasks to dedicated cyber engineering teams, and conducting regular team retrospectives to reflect and identify areas for enhancement. Individually, each method is easy to implement; together, they create a robust system that safeguards engineering time, ensures improvement work is grounded in frontline experience and channels tasks to the right owners for execution.
Embracing lean teamwork and stakeholder alignment
When it comes to applying lean people and teamwork principles in cybersecurity, agile methodologies offer a practical and effective implementation vehicle. While there is no definitive evidence that Agile directly improves threat response speed, it can significantly enhance collaboration and alignment with the business. Team collaboration, business alignment and change adaptability can help isolated security teams regain visibility and produce value-added services.
Team collaboration is the first critical area that isolated security teams must address. These teams tend to operate in silos due to the specialised nature of their work, where deep technical expertise is required within narrow domains. This specialization, while necessary, can lead to fragmentation. Agile counters this by promoting regular interaction and shared ownership, helping teams maintain cohesion and reduce operational isolation.
Business alignment is another critical area. Security teams typically operate at full capacity, with a strong focus on mission-critical tasks and limited bandwidth for broader stakeholder engagement. Over time, this can lead to a disconnect between security objectives and business priorities. Agile helps close this gap by encouraging frequent stakeholder touchpoints and promoting transparency in planning and delivery.
Change adaptability is essential in the fast-moving cybersecurity landscape. Traditional project management methods, with fixed scopes and long timelines, often fall short in responding to rapidly evolving threats. Agile’s iterative approach—delivering value in smaller, faster cycles—enables security teams to remain responsive and adaptive as priorities shift.
Finally, an “eat your own dog food” approach aligns closely with the Go-See principle in lean manufacturing. It requires all members of the cybersecurity team (management included) to directly experience the tools, processes and systems they design and manage. This engagement promotes an understanding of operational constraints, uncovering friction points, inefficiencies or tooling issues that struggle to surface. When engineers, analysts and leaders use their solutions in live environments, they are better equipped to identify real-world problems and drive meaningful, experience-based improvements across all layers of the security organization.
Together, these Agile practices help embed lean principles into the core of cybersecurity operations, enabling teams to work more cohesively, stay aligned with the business, and adapt to change with greater efficiency.
Delivering high-quality cybersecurity output
On the continuous improvement front, cybersecurity teams must adopt a systems thinking approach to consistently visualize, inspect and refine their operational processes. Time and budget constraints are the norm in security operations, making it critical to uncover and eliminate inefficiencies with precision. Only through the relentless reduction of waste can teams free up capacity and build the methodology needed to see the bigger picture and drive impactful, sustainable improvements.
Systems thinking is, at its core, a simple yet powerful mindset. It starts from the premise that every system is perfectly designed to produce the results it currently delivers. Poor systems will consistently generate poor outputs, while well-designed systems yield reliable, high-value outcomes. It is the responsibility of system owners to analyse their processes, treat them as dynamic systems and identify inefficiency.
Each operational process should be seen as a system within the broader cybersecurity program, which itself is a system of systems. Just like a racing engine, where fuel, cooling and electronic systems must all be tuned to extract peak performance, cybersecurity programs require every process to be optimized in concert to achieve lean and agile operations.
In systems thinking, each system is defined by three key components:
- Elements: These are the individual parts or resources of the system (people, tools, processes, data or assets) that collectively form its structure.
- Interactions: These describe how elements connect and influence one another, through workflows, causal loops or control mechanisms.
- Purpose: This is the goal or function the system is intended to achieve such as detecting and responding to threats or reducing company risks.
By analyzing systems in terms of their elements, interactions and purpose, engineering teams can identify constraints on optimal performance. They can also analyse where improvements in one system may positively or negatively impact another. Systems thinking enables teams to understand how things work while fostering ownership and continuous improvement of their processes. This approach is foundational to building a lean, agile, and high-performing security program.
As part of a systems thinking approach, cybersecurity teams may use causal loop diagrams to map out the relationships between key elements in their operations and uncover how different actions and outcomes influence one another over time. By documenting these feedback loops (both positive and negative) teams can identify where constraints, bottlenecks or unintended consequences are occurring. For example, a reinforcing loop between alert fatigue and missed detections may reveal a need for better triage automation. Causal loops help teams shift from symptomatic fighting to meaningful root-cause analysis, enabling more targeted improvements across operations.
Conclusion
In conclusion, lean cybersecurity is a practical framework for security teams to balance operational demands with the need to deliver business value. Inspired by the foundational principles of lean manufacturing, this approach encourages waste reduction, workflow optimisation and alignment with stakeholders. Through workload levelling, structured collaboration, agile execution and systems thinking, teams can transform reactive operations into proactive, high-impact programs.
More importantly, lean cybersecurity is not only simple to implement, but it also scales effectively when supported by consistent execution and strong team commitment. By embedding lean principles at the core of their strategy, cybersecurity teams build programs that are resilient, efficient and fully integrated with changing business needs.
